- Data Management
- Security and Compliance Studio
- Concepts
In Security and compliance studio, you can manage which securable objects have access to sensitive data. For each securable object, you can:
- Give access to sensitive data. All related securable objects automatically inherit access.
- Undo access to sensitive data. Access is automatically undone for all related securable objects.
The following rules define how sensitive data access inheritance works:
- If you give a securable object access to sensitive data, all entry points linked to that securable object also get access. As a result, all securable objects with access to these entry points inherit access to the sensitive data.
- If you undo sensitive data access for a securable object, all linked entry points lose access. Consequently, all securable objects with access to these entry points also lose access. However, if a securable object still has another entry point with sensitive data access, its access remains.
Example 1
Give 'Privilege 2' access to sensitive data.
'Entry point 4' already has access to sensitive data.
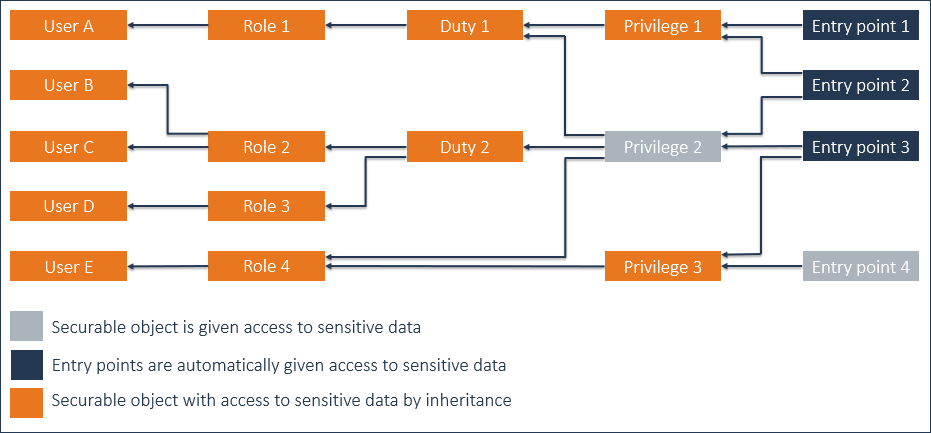
As a result of giving 'Privilege 2' access to sensitive data:
- Entry points 2-3 are given access to sensitive data.
- By inheritance, Privilege 1, Duties 1-2, Roles 1-3, and Users A-D are given access to sensitive data.
- As Privilege 1 is given access to sensitive data, Entry point 1 is given access to sensitive data as well.
- Privilege 3, Role 4, and User E already had access to sensitive data, inherited from Entry point 4. So, nothing changes for these securable objects.
Example 2
The result of Example 1 is the starting point.
Undo access to sensitive data for Duty 2.
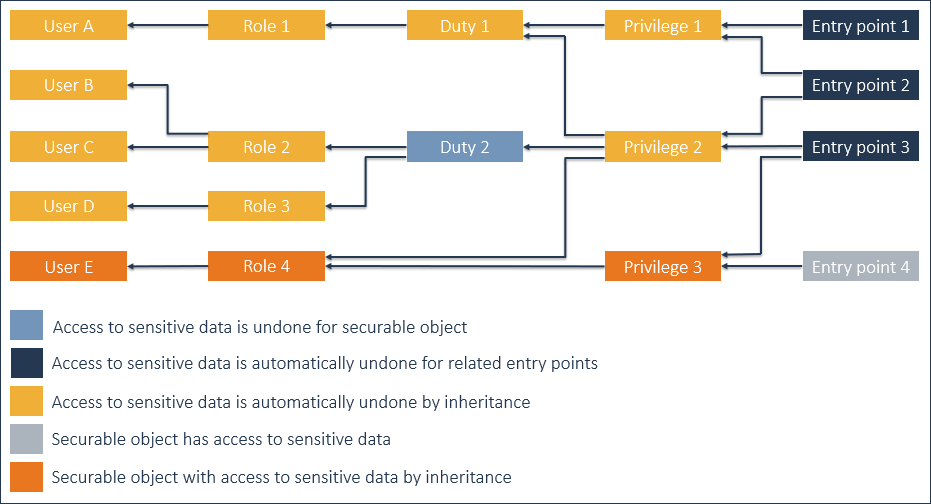
As a result of undoing access to sensitive data for Duty 2:
- Access to sensitive data is undone for Entry points 2-3.
- By inheritance, access to sensitive data is undone for Privileges 1-2, Duty 1, Roles 1-3, and Users A-D.
- As access to sensitive data is undone for Privilege 1, also access to sensitive data is undone for Entry point 1.
- Privilege 3, Role 4, and User E have access to sensitive data, inherited from Entry point 4. So, nothing changes for these securable objects.